Security Control Room Best Practices
Control room security is more crucial than ever, as these hubs are vital for managing critical infrastructure. s cyber threats evolve, so do the demands for stringent security measures. With the implementation of the new EU directive NIS2 set for October 2024, organizations must prepare for increased legal requirements surrounding cybersecurity.
Understanding NIS2 and Its Implications
The NIS2 directive focuses on enhancing cybersecurity across the EU, particularly for critical infrastructure sectors. This means that operators, contractors, and suppliers will need to prioritize information security. The directive emphasizes supply chain security, requiring organizations to ensure that their suppliers and service providers meet specific security standards. Here are some key requirements for suppliers and integrators outlined in NIS2:
- Products: Ensure security during IT procurement.
- Suppliers: Control and monitor the security practices of service providers.
- Supply Chain: Establish protocols for supply chain security.
Guidelines for IT Procurement : NIS 30.2.5a
For critical infrastructure, it’s essential to maintain rigorous security standards during the procurement process. The NIS2 directive outlines the following requirements:
- Implement protective measures.
- Ensure compliance with recognized standards.
- Verify that development and code adhere to established security protocols.
- Require that products be tested and certified for security.
Supply Chain Management
Effective supply chain management is critical. Organizations must:
- Define mandatory security requirements for suppliers.
- Monitor compliance through thorough documentation and verification.
Supply Chain Security: NIS 30.2.4b
In addition to securing service provider relationships and products, NIS2 also focuses on supplier and service provider resilience.
- Avoid single points of failures
- Dependencies on suppliers and service providers
Common Security Concerns in Control Rooms
Control rooms face several security challenges, including:
- Insider Threats: Risks posed by employees or contractors.
- Physical Security: Protecting entry points and ensuring surveillance.
- Cybersecurity Threats: Safeguarding against hacking and malware.
- Unauthorized Access: Preventing access by unauthorized personnel.
Technological Vulnerabilities
Control rooms are often vulnerable to various technological risks:
- Outdated Software: Using unsupported software can create security gaps.
- Network Security: An unsecured network can lead to breaches.
- Data Protection: Lack of encryption can expose sensitive information.
Best Practices for Security
To mitigate risks, control rooms should adopt several best practices:
- Access Control: Implement strict access measures for sensitive data and systems.
- Regular Audits: Conduct frequent security audits to identify and rectify vulnerabilities.
- Employee Training: Ensure all staff are trained on security protocols and threat recognition.
- Incident Response Plan: Develop and maintain a comprehensive incident response strategy.
System Security Best Practices
- Firewall Protection: Regularly update firewall rules.
- Network Protection: Lock down switch ports and use DHCP cautiously.
- Isolation and Segmentation: Separate critical data and networks.
- Device Protection: Utilize endpoint protection to fend off attacks.
- User Rights Management: Regularly review access rights.
- Vulnerability Management: Keep systems updated with the latest software.
- Data Encryption: Implement encryption to protect sensitive information.
- Trusted Software: Restrict access to boot settings and ensure software is signed.
- Security Configuration: Disable unnecessary services and enforce best practices.
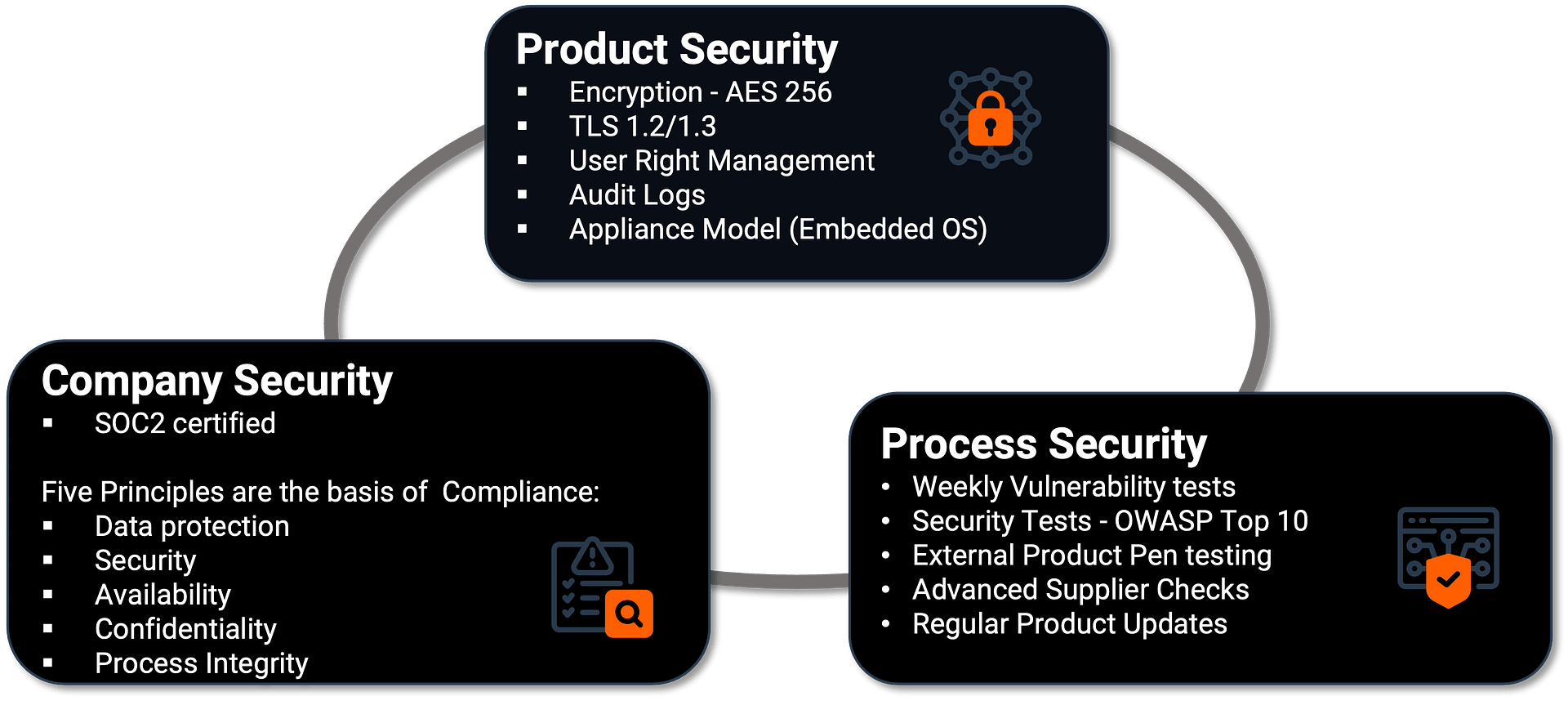
How VuWall Ensures Security
ISO 27001 vs. NIST vs. NIS2 vs. SOC 2
ISO 27001 is an international standard and can be applied to any industry.
NIST is a voluntary framework primarily used in the United States
NIS2 is a mandatory directive for EU member states, aiming to harmonize cybersecurity practices
SOC 2 is the preferred certification for SaaS or Software companies and is mostly relevant in North America but rapidly expanding globally.
VuWall has been certified with SOC2 because we are, primarily, a software company.
Summary
As the threat landscape continues to evolve, control rooms must remain vigilant and proactive in their cybersecurity efforts. By understanding the implications of NIS2 and implementing best practices, organizations can enhance their security posture and protect critical infrastructure from emerging threats. Investing in robust security measures not only safeguards operations but also fosters trust among stakeholders in an increasingly interconnected world.
 English
English Deutsch
Deutsch Français
Français Español
Español